
Cloud Computing Security: Essential Best Practices for Protecting Your Data
Advertisment
Cloud Computing Security: Essential Best Practices for Protecting Your Data
As businesses increasingly migrate to Cloud Computing, security concerns have become a top priority. While cloud providers implement robust security measures, organizations must also take proactive steps to safeguard their data and applications in the cloud. This article delves into the best practices for enhancing Cloud Computing security and mitigating potential risks.
1. Understanding Cloud Security
1.1. What is Cloud Security?
Cloud Security encompasses the policies, technologies, and controls used to protect data, applications, and infrastructures involved in Cloud Computing. It addresses the risks associated with data breaches, unauthorized access, and compliance violations.
1.2. Shared Responsibility Model
A fundamental concept in Cloud Computing security is the shared responsibility model. While cloud providers are accountable for securing the infrastructure, organizations must secure their data, applications, and user access. Understanding this model is crucial for effective risk management.
Keywords: Cloud Security, shared responsibility model, data protection
2. Best Practices for Cloud Security
2.1. Implement Strong Access Controls
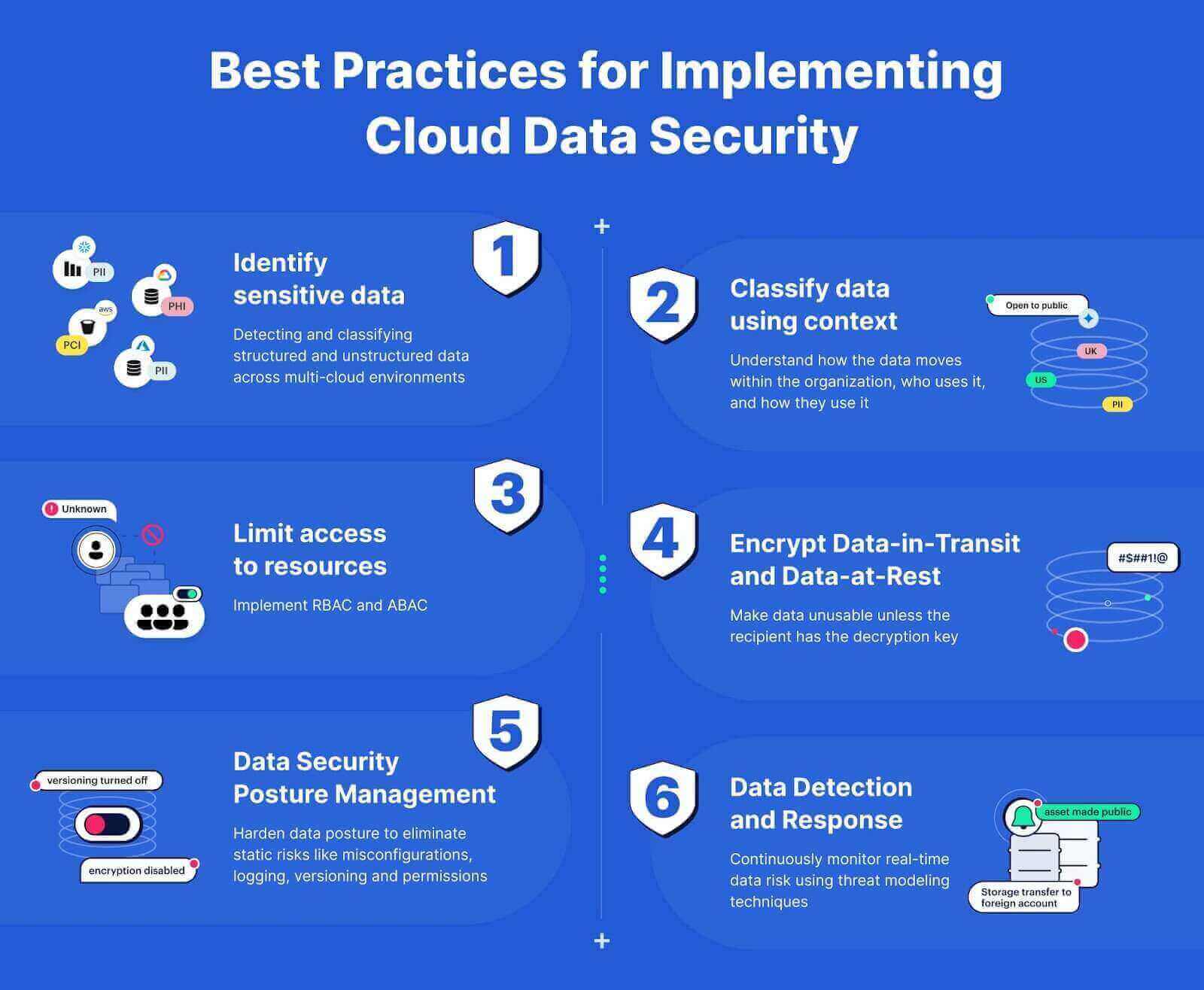
- Role-Based Access Control (RBAC): Assign permissions based on user roles to limit access to sensitive data and applications. This ensures that only authorized personnel can access critical resources.
- Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security. Requiring users to provide two or more verification factors can significantly reduce the risk of unauthorized access.
Keywords: access controls, role-based access, multi-factor authentication
2.2. Encrypt Data
- Data Encryption: Encrypt sensitive data both in transit and at rest. This ensures that even if data is intercepted or accessed by unauthorized users, it remains unreadable.
- Key Management: Establish a secure key management strategy. Properly managing encryption keys is essential for maintaining data security and compliance.
Keywords: data encryption, key management, data security
2.3. Conduct Regular Security Audits
Perform regular security audits and assessments to identify vulnerabilities within your cloud infrastructure. This proactive approach allows organizations to address potential security gaps before they can be exploited by attackers.
Advertisment
Keywords: security audits, vulnerability assessment, proactive security
2.4. Monitor Cloud Resources
Utilize continuous monitoring tools to track access and activity within your cloud environment. Monitoring can help detect unusual behavior or unauthorized access attempts in real time, enabling rapid responses to potential threats.
Keywords: monitoring, cloud resources, threat detection
2.5. Establish an Incident Response Plan
Having a well-defined incident response plan is critical for minimizing damage in the event of a security breach. This plan should outline roles, responsibilities, and procedures for responding to incidents, ensuring that the organization can act quickly and effectively.
Keywords: incident response, security breach, response plan
3. Compliance and Regulatory Considerations
3.1. Understanding Compliance Requirements
Organizations must be aware of compliance requirements related to their industry, such as GDPR, HIPAA, or PCI-DSS. Understanding these regulations is essential for implementing appropriate security measures and avoiding penalties.
3.2. Collaborating with Cloud Providers
Work closely with your cloud provider to ensure compliance. Most reputable providers offer compliance certifications and resources to help businesses meet regulatory requirements.
Keywords: compliance requirements, regulatory considerations, cloud provider collaboration
4. Employee Training and Awareness
4.1. Security Training Programs
Invest in regular security training for employees to raise awareness of potential threats and best practices. Training should cover topics such as phishing, password security, and safe data handling.
4.2. Foster a Security-First Culture
Encouraging a culture of security within the organization can significantly reduce risks. Employees should feel empowered to report suspicious activity and understand the importance of following security protocols.
Keywords: employee training, security awareness, security culture
5. Conclusion
Cloud Computing offers substantial advantages, but security remains a critical concern. By implementing best practices such as strong access controls, data encryption, regular security audits, and employee training, organizations can significantly enhance their Cloud Computing security posture. Proactive measures will help mitigate risks and protect sensitive data, ensuring a secure and efficient cloud environment.
Advertisment









Post Comment